
In today’s time, the majority of software development teams are using Microservices architecture as their default approach to creating modern applications. But in order to avail all the benefits of the microservices, the development team needs to have a proper understanding of both the bright and the dark side of microservices. Designing perfect microservices is not only about writing the application in small pieces but also about managing complicated networking and securing the microservices. To know more about microservices security and see how software development companies can implement various microservices best practices for security, let’s go through this blog.
1. What is Microservices Security?
Microservice security is one of the most important strategies that every software development and security team uses in order to reduce the number of risks that are associated with microservices architecture. Here, the security efforts mean making sure that the communication between the microservices is built clearly and they are safe.
Besides this, when it comes to microservices or any other independent software component, deploying it separately is possible but the developers need to make sure that the process is efficient, especially for the large-scale application. The main reason behind this is that every independent service can be quickly updated and to cope with that frequent changes, the developers need to choose the right technology stack for each and every individual component. As the software developers can deploy microservices independently from each other, it enables companies to scale various aspects of the application without actually scaling the entire application by reducing the cost and usage of resources.
2. Ways to Secure Microservices
Here are some of the popular ways that can help software development teams secure microservices in the best manner.
2.1 Make your Microservices Architecture Secure by Design
The very first practice for securing microservices is to make their architecture secure by design. The majority of the applications that are based on a microservice are deployed when any business organization wants to modernize its monolithic systems. Therefore, the design phase is the best choice to start making the legacy system secure. This is why the security and development teams must prioritize securing the application when designing a microservices architecture as it enables the app to have a proper foundation.
Besides this, when it comes to designing secure software, security is a must at every level of the application which actually starts from its microservices architecture. For this, the developers use threat modeling as it enables them to examine the design of operations of the entire system and check how the data flows through microservices. This approach helps software developers to identify the weakness of the system and remove it during the design phase. In addition to this, in microservices architecture, it is essential for the developers to create highly secure code and use open-source components that are hardened against any risk.
Further Reading on Monolithic vs Microservices Architecture
2.2 Secure Authentication
When it comes to securing microservices, authentication is a must-have as microservices generally access sensitive data of any business organization which can not be misused. Therefore, app development companies prefer to use unique ways of authentication for microservices API keys. Here, some services might require short-lived tokens and some might require usual to safeguard them or limit the damage. Basically, authentication tokens that are used by the developers must be cryptographically signed, handle-based, or have the protection of an HMAC scheme.
To secure the microservices, every authentication API key that is used by the software development team must have restrictions specified to it as per the application and the set of APIs used in it. Besides this, when it comes to stateless authentication tokens like JSON Web Tokens, the developers must implement them using shared libraries that are related to the services and must follow security precautions like token key must not be an element of the library code and expiry time of token must be short.
2.3 DevSecOps Strategies
One of the main advantages of using microservices for your project is that it enables the software development teams to work rapidly on deploying individual components of the software without any requirement of redeploying them in the entire application. This means that the DevOps experts can quickly create an application at a faster rate and can get time to look at the security risks before deploying it. This is how it helps the development team to shift their mindset towards dynamic analysis security testing and static analysis security testing of each and every component of the application during the development process. This is why when it comes to utilizing DevSecOps approaches in the development process where the security measures are directly integrated is possible.
This approach offers constant integration of the DevSecOps strategies in the development process and helps in reducing the security risk factors of the application. Besides this, DevSecOps has the capability to call for automation and enable the creation of a shared responsibility that eventually helps in delivering secure software.
Basically, utilizing the DevSecOps approach is one of the best practices to follow while securing microservices as this concept can even help in reducing the time and cost that goes behind securing the software deployment process as it allows developers to deploy the software at one go.
2.4 Create API Gateways
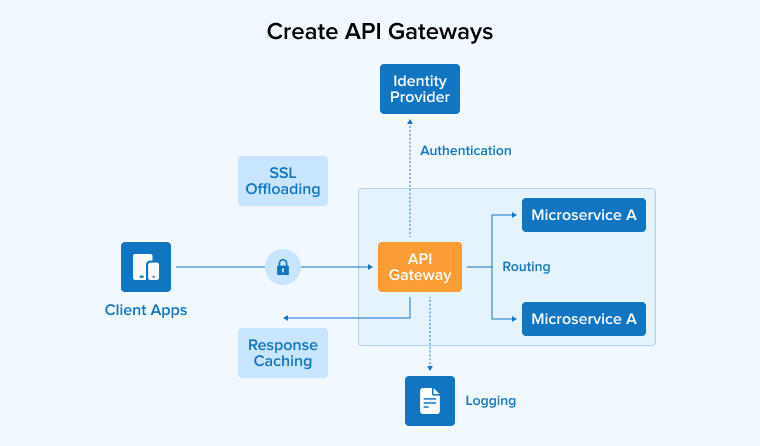
Another method used for microservices security is creating an API gateway. This is known as the most commonly used method. It enables the developers to create a single entry point in the system for all external access requests that come as they are known as the most susceptible to attacks. There are many different API gateways available in the market like Amazon API Gateway which comes with various security features and management approaches that can help authenticate the application. Besides this, such API gateways also help limit the rate that goes behind protecting the application from huge traffic and unauthorized access that happens. In addition to this, the API gateway also enables authorization with most components of microservices.
2.5 Access Management Security Strategies
Access management is an essential way to secure microservices and for that policies that can safeguard the APIs must be defined & provisioned to an access server. At a coarse level of granularity, it is said that access policies must specify the “Permit to Call” for the defined set of addressable functionalities. Besides this, the caching mechanism in the access management strategy must be able to enable microservices to cache the data of the policy specified for it. In addition to this, the cache must only reply when the access server is not available to carry out the service and once the cache is opened, it must expire after some time.
While strategizing the access management security policy, one thing that must be taken into consideration by the development team is that the access server should have the ability to support fine-grained policies. The access decisions must be conveyed to a set of microservices and individuals as per the standardization or the format of the services.
2.6 Secure Communication
One of the most important strategies that every software development company working with microservices should take care of is securing the communication between the client and the services. Though there are some security service strategies like authentication and secure connections for handling individual microservices nodes, a secure SSL/TLS connection is a must for every microservice to protect its interservice or inter-process communication. This security is applied by considering the overall application’s perspective.
Besides this, the SSL/TLS connection can be created dynamically before each interservice request is made by the application. When the developers have created an application that follows the keep-alive connection approach, one service will create a connection only after a full SSL/TLS handshake at the initial stage and then it will send a request to another service. In this case, if either of the services doesn’t terminate the connection, then the same connection can be used in the future. This scheme is used for cost-saving purposes.
2.7 Ensure Container Security
Software development teams generally use containers for microservice applications in order to deal with various different components that can help in making software development an easy process. The security vulnerabilities with containers include configuration and isolation faults, compromised images, and other security risks in the host operating system, which might have all the containers running on it. Therefore, in this case, the experts try to use the security principle that is of the least privilege with the strategies below-
- Defining rules to isolate the access of all the resources.
- Not using privileged accounts or Sudo in order to run the services in the application.
- Restricting the authorization to the minimum requirements.
- Avoiding the storage of any development secrets on container disks.
Besides this, developers use container orchestration tools like Kubernetes to automate the scaling, security posture, and deployment of the containers. Therefore, if the developers follow the best practices for Kubernetes security along with authorization approaches, the deployment process can go smoothly in a highly secure manner.
2.8 Implement Dependency Scanning
Another beneficial way to secure microservices is to implement dependency scanning. Microservices and modern software solutions both use a large number of open-source components which means that the entire application will start depending on far outweighs which are written by the development teams. And such types of open-source, third-party dependencies come with various different types of vulnerabilities that can impact the entire application and also risk the users’ profiles. Besides this, the open-source code is generally written by the developers using individual microservices which makes it even more difficult for any app developer to track third-party components and ensure their security.
In this case, it becomes really important to use open-source security management tools that can help in finding risks and fixing potential vulnerabilities in the open-source app development code.
2.9 Control Internal Communications Between Microservices (East-West)
Another way to secure microservices in any application is to secure the communication between the services. To implement security aspects of inter-service communication, there are many different ways available in the market that are quite difficult to implement compared to external consumer traffic (north-south). The reason behind this is that in inter-service communication both the service provider and the client reside in an internally secured network, the security requirements differ which means that the developers might have to apply hard security or any other general type of security aspects. Here are different types of security implementation approaches that can be used to safeguard east-west traffic.
Transport Layer Security
The transport layer security approach is known as the least secure concept with SSL enabled for communications that happen between the messaging platform and microservice. Here, both microservice and messaging platforms are present in a secured LAN which means that transport layer security can be applied. You can use this approach.
Transport Layer Security with Message Layer Security using Authentication
Another method is to implement transport layer security along with message layer security. This approach is implemented if the previous approach is not secure enough for any organization’s application. The developers can implement microservices authentication for communication as it helps ensure that the microservices with valid credentials will only be able to communicate with the messaging platform or with any other microservices.
Transport Layer Security with Message Layer Security using Authentication and Authorization
The third type of security approach used to safeguard inter-service communication is to use both authorization and authentication aspects with transport layer security. Here the communication is taken into control by using an authorization scheme that specifies what a microservice can access in the application.
2.10 Control Access to Microservices (North-South)
Now, let us have a look at the ways that can be used to control access to microservices. Here the microservices are secured from external consumers as it is the most vulnerable path in any application. In order to implement security for external-service communication (north-south traffic) by using different approaches, follow the below-given methods.
Implement Security at Each Microservice Level
The very first way to implement external-service communication is to implement security at each level of microservices as because of the polyglot nature of microservices development, there will be various teams that will work on their own choices of programming languages and microservices frameworks for implementing security. In such cases, implementing security for each level of microservice can be very beneficial to adhere to a common security standard.
Implement Security using a Sidecar
Another approach is to implement security with the use of a sidecar. This means that here the developers use an external framework like Open Policy Agent (OPA) or Istio to implement the security at each level of a service and then that security component will run with the service as a sidecar.
Implement Security using a Shared Gateway
The last approach which can be used to secure external-service communication is by implementing security for microservices that make use of a shared component and implementing security for individual microservices. In this approach, the shared component can be a security gateway or an API gateway that will be present in the front of the microservices layer to secure the service of any application.
3. Microservices Security Challenges
Here are some of the challenges that any software development company will have to face while securing microservices.
3.1 Isolation
Generally, it happens that any microservices application will rely on isolation when it comes to creating, testing, deploying, and scaling an application in a manner that a microservice doesn’t affect another microservice. For this, the software developers have to implement isolation at the database level which eventually helps in ensuring that each microservice will have its own data that cannot be used by other microservices. Implementing isolation at all layers is very difficult.
3.2 Increased Attack Surface
Every microservice creates communication with the use of APIs which is independent of programming language and machine architecture. This increases the chances of an attack on the surface of the application. Besides this, interactive services are used in the system, they can also make it critical for the application to run smoothly. Therefore, the software security teams need to stay ahead and track the microservices that break the operations.
3.3 Caching
Another microservices challenge is caching. Caching is something that can help in reducing the frequency of requests that are made by the client side. But when the caching requests grow and it becomes difficult to handle other services, this excess reserve will increase the level of complexity in the application and will also affect the amount of inter-service communication. This is when the software developers will have to face this challenge by automating, ordering, and optimizing this communication.
4. Concluding Words
As seen in this blog, microservices generally rely on distributed components in order to offer various advantages like deployment and flexibility. But, when the developers are using microservices for application development they need to take care of internal security policies & strategies and adjust them to have a distributed and cloud-native approach. This can help the development teams reduce the attacks that happen on microservices and can protect them along with the applications and APIs.






Comments
Leave a message...